What Is Security Monitoring? Importance and Tools

It is impossible to overestimate the importance of security monitoring in an organization’s cybersecurity strategy in the digital era, as cyber threats are growing more complex and widespread. One essential tool for assisting businesses in identifying, evaluating, and mitigating any security risks before they cause serious harm is security monitoring. This thorough review delves into the meaning, significance, and necessary security monitoring technologies, as well as their critical function in protecting enterprises.
The Meaning and Significance of Security Surveillance
The process of identifying and managing potential security threats or vulnerabilities by continuous collection, analysis, and escalation of various indications and warnings is known as security monitoring. By identifying unusual activity that can point to a security breech or hack, it’s a preventative strategy that helps companies stay one step ahead of fraudsters.
The ability to offer real-time visibility into an organization’s security posture is what makes security monitoring so important. Organizations can reduce the risk of data loss, financial loss, and reputational damage by promptly identifying possible security issues and evaluating data from several sources inside the IT system.
The Meaning and Significance of Security Surveillance

Organizations are safeguarded by security surveillance, which provides a comprehensive perspective on their security environment. It allows IT security teams to:
- Detect and Respond to Threats: Rapidly identify and mitigate threats before they escalate into significant breaches.
- Compliance and Regulatory Adherence: Monitor for compliance-related anomalies to ensure that the organization complies with legal and regulatory requirements.
- Operational Efficiency: Enhance the efficiency of security operations by automating monitoring and analysis, enabling security teams to concentrate on strategic duties.
Main Goals and Advantages of Security Monitoring
Security monitoring is primarily concerned with the early detection of unauthorized access or malevolent activities, the reduction of security breaches, the preservation of data integrity and confidentiality, and the availability of IT services. However, the advantages surpass mere threat detection:
- Security Posture Enhancement: Organizations can fortify their defenses against potential attacks by consistently monitoring threats.
- Reduced Incident Response Time: Rapid detection of anomalies allows for speedier response, reducing the impact of security incidents.
- Increased Operational Efficiency: Automated tools and processes expedite the detection and response to security events, freeing valuable resources.
- Compliance and Regulatory Fulfillment: Helps organizations adhere to industry standards and regulatory requirements by providing evidence of continuous monitoring and protection efforts.
Monitoring Security and Detecting Intrusions
An essential component of efficient security monitoring are intrusion detection systems, or IDS. Network traffic and system activity are closely examined by these systems to look for indications of malicious activity or policy violations. IDS is divided into two categories: host-based (HIDS) and network-based (NIDS). Both play complimentary but distinct functions in the ecosystem of security monitoring. IDS plays a critical role in the larger security monitoring strategy by warning security staff of possible threats and allowing enterprises to act quickly to reduce risks.
Main Categories of Security Surveillance

Security monitoring serves as a sentinel against the ever-evolving dangers that companies confront on a daily basis in the wide and complex cybersecurity landscape. It includes a range of tactics and instruments intended to identify, evaluate, and address possible security events. Creating a thorough security posture that guards against a variety of cyberthreats requires an understanding of the main categories of security monitoring. The primary categories of security monitoring are discussed below; each has a distinct function within the overall cybersecurity framework.
Monitoring of Network Security
Network traffic analysis is done as part of Network Security Monitoring (NSM) to find potentially dangerous activity and suspicious activity. Organizations can identify anomalies, including irregular data transfers or unauthorized access attempts, that may point to a security breach by regularly monitoring inbound and outbound traffic. Security teams may quickly detect and eliminate threats before they become major incidents by using NSM technologies, which offer real-time visibility into network activities.
Monitoring of Endpoint Security
Endpoint security monitoring has become essential due to the increase in devices connected to business networks, such as laptops, smartphones, and Internet of Things devices. With this type of monitoring, the devices themselves are the main focus. Malware infections, unauthorized alterations, and other security concerns are found and addressed at the device level. Businesses may drastically lower their attack surface by making sure every endpoint complies with security guidelines and is secure.
Monitoring of Application Security
Applications are frequently an organization’s lifeblood, but they may also be easy targets for hackers. Examining applications for anomalous activity, such as unexpected data access patterns or alterations in user behavior, that may point to a compromise is known as application security monitoring. This kind of monitoring aids in making sure that applications—whether created internally or purchased from outside parties—remain safe from the beginning to the end, from creation to deployment and upkeep.
Monitoring of Database Security
Strict security measures are needed for databases that contain the valuable data that fraudsters are after. By monitoring access to and modifications to the data, database security monitoring aims to safeguard these vital resources. It entails keeping an eye out for actions that might indicate a data breach, such as privilege escalation and unauthorized access attempts. By taking a proactive stance, sensitive data is protected from external and internal risks.
Log Keeping and Administration
For security monitoring, logs—which are produced by a variety of devices, systems, and applications—offer a wealth of information. The process of gathering, examining, and archiving logs in order to spot patterns, uncover irregularities, and look into security issues is known as log monitoring and management. Organizations can get a comprehensive picture of their security posture by combining data from several sources, which makes it simpler to identify and fix possible risks.
Monitoring of Cloud Security
There is a growing need for cloud security monitoring as more businesses move to cloud-based services. The particular difficulties presented by cloud computing—such as multi-tenancy, dynamic resource allocation, and the shared responsibility model—are addressed by this kind of monitoring. By giving enterprises visibility into cloud environments, cloud security monitoring technologies help them identify security flaws, unauthorized access, and other problems with their cloud installations.
Monitoring of Identity and Access
To guarantee that only people with permission can access sensitive systems and data, identity and access monitoring is essential. This entails keeping an eye on user behavior and access patterns in order to spot any irregularities that might point to an insider threat or compromised account. Businesses may reduce the risk of data breaches and stop unwanted access by putting strong authentication procedures in place and keeping an eye on user behavior.
Monitoring Compliance
Complying with ever-increasing privacy and data protection regulations has made compliance monitoring an essential part of security monitoring. This kind of oversight guarantees that companies follow industry guidelines and legal requirements, such GDPR, HIPAA, and PCI DSS. Organizations can avoid expensive fines and reputational harm associated with non-compliance by regularly checking compliance status.
Patching and Vulnerability Management
A crucial component of security monitoring is vulnerability and patch management, which focuses on finding, evaluating, and reducing vulnerabilities in systems and software. Organizations can guard against fraudsters taking advantage of them by routinely checking for vulnerabilities and implementing the required updates. By decreasing the window of opportunity for attackers, effective vulnerability management improves the organization’s overall security.
Every kind of security monitoring is essential to an organization’s all-encompassing security plan. Organizations may guarantee strong defense against a broad range of cyber threats by putting into practice a multifaceted strategy that incorporates network, endpoint, application, database, log, cloud, identity and access, compliance, vulnerability, and patch management.
Patching and Vulnerability Management
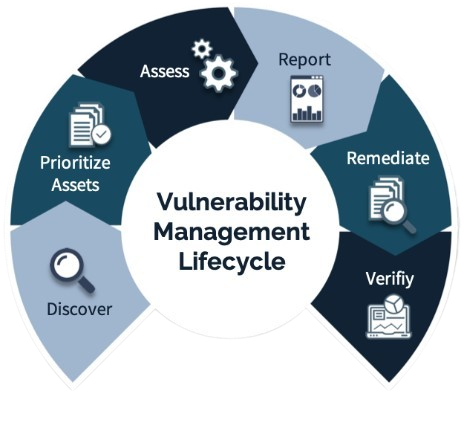
It is impossible to overestimate the significance of security monitoring in protecting an organization’s assets as the digital landscape changes. Businesses now need to implement strong security monitoring procedures due to the rise of sophisticated cyber threats and growing reliance on digital platforms. The importance of security monitoring in today’s security environment is examined in this section, along with its advantages and critical function in preserving the confidentiality, availability, and integrity of organizational data.
How Can Monitoring for Cybersecurity Benefit Your Company?
Beyond only identifying dangers, cybersecurity monitoring has many other advantages. It gives a thorough picture of an organization’s security position, empowering decision-makers and improving resource allocation. Organizations can decrease the probability of successful assaults via early detection of possible threats by constant monitoring for suspicious activities. By taking a proactive stance, companies can safeguard confidential information, preserve operational continuity, and preserve their standing with stakeholders and consumers.
Addressing Security Risks
When dealing with a security threat, timing is critical. Organizations that use security monitoring are armed with the knowledge and resources needed to react to possible problems quickly and efficiently. Security teams may quickly start response measures by identifying anomalies that could indicate a breach or an attempted attack by continuously monitoring data from several sources. By reducing the effect of security issues, this quick response capability shields the company and its clients from possible harm.
Cut Down on Data Breach
Data breaches can have disastrous effects, such as monetary losses, harm to one’s reputation, and legal implications. By seeing threats and weaknesses before they can be exploited, security monitoring is essential in lowering the risk of data breaches. Organizations can prevent unwanted access to sensitive information by detecting and addressing security gaps through continuous monitoring of networks, systems, and applications.
It Assists in Preventing Delays
Security events can result in major delays in business operations, revenue loss, and process disruptions. Establishing efficient security monitoring can help firms prevent the downtime brought on by security breaches. Businesses may respond quickly to risks by using real-time alerts and continuous monitoring, which guarantees uninterrupted operations.
Reduce Your Security Susceptible
Organizations can find and fix vulnerabilities through security monitoring before an attacker can take use of them. Businesses can drastically lower their security vulnerabilities by regularly searching for flaws and applying patches and upgrades on schedule. This proactive approach improves the organization’s entire security posture in addition to providing protection from external attacks. Furthermore, it is more realistic to accept that security breaches will inevitably occur rather than holding the belief that all unwanted access can be stopped. The best strategy is, in reality, to prioritize quick recovery techniques.
It Aids in Adhering to Regulations
One of the most important things for many firms is compliance with regulations. By demonstrating adherence to security best practices and due diligence, security monitoring bolsters compliance efforts. Businesses can meet regulatory requirements and stay out of trouble by keeping track of security occurrences and proving that they are committed to continuous security monitoring.
Cuts Down on Downtime
An organization’s income, customer satisfaction, and operational efficiency can all be severely impacted by downtime. Unplanned downtime is frequently caused by security incidents since they can interfere with corporate operations and necessitate drawn-out repair activities. By offering real-time alerts and insights into potential threats, security monitoring reduces the chance of downtime and empowers organizations to proactively address vulnerabilities and promptly respond to events. Through the implementation of robust and secure systems, regular backups, extensive testing, and quick recovery, businesses may minimize downtime expenses and sustain uninterrupted operations.
It Stops Unauthorized Entry
Theft of intellectual property, data breaches, and compliance issues can result from unauthorized access to company networks and sensitive data. By constantly keeping an eye on user behavior and access patterns, security monitoring stops unwanted access. Security teams can respond quickly when advanced monitoring technologies identify unusual activity that could point to a compromised account or insider threat. Organizations may greatly improve their security posture and safeguard their assets from unauthorized individuals by putting strict access controls in place and regularly checking for compliance.
It Supports Sustaining Firm Stability
An organization’s capacity to control and minimize risks has a direct impact on its stability. By offering a thorough understanding of the organization’s security environment, spotting any dangers, and assisting with well-informed decision-making, security monitoring helps to maintain this stability. Businesses may steer clear of the chaos brought on by security incidents, including monetary losses, harm to their brand, and legal issues, by taking proactive measures to address security problems. RedZone Technologies wants to free you up to concentrate on offensive by helping with defense, which means that long-term success and expansion depend on the maintenance of a stable and secure environment.
Boost Employee Productivity
Security events have the potential to take resources away from essential company operations, which lowers output. Workers can be obliged to handle attack fallout, including lost data or unavailable systems, instead of concentrating on their main duties. By ensuring that systems are accessible and secure, security monitoring helps to minimize these disturbances and free up staff members to work productively and uninterrupted. Furthermore, companies can improve staff morale and lessen stress related to possible security issues by promoting a secure work environment.
Strong Security Promotes Scalability and Contract Wins
Strong security is a competitive advantage as well as a defensive strategy. Demonstrating a commitment to security can be a crucial differentiator for companies seeking to grow. By ensuring that an organization’s security measures expand with its size, security monitoring helps to mitigate the increasing risk exposure that comes with growth. Furthermore, exhibiting thorough security monitoring capabilities can be a deciding factor in getting contracts in companies where security is a top priority. Businesses that prioritize security have a higher chance of gaining the trust and cooperation of their clients and partners because they see it as a sign of dependability and professionalism.
