An Introduction to Cloud Network Technology : Types and Advantages

Cloud Network Technology : What is it?
A major development in contemporary computing, cloud network technology redefines the management and delivery of data, apps, and services via the internet. This technology, which enables effective resource utilization, scalability, and communication across several platforms and devices, is essential to cloud computing.
Cloud Network Technology Definition
The term “cloud network” describes the infrastructure that makes it possible to supply computing services—such as servers, storage, databases, networking, software, and analytics—over the internet, or “the cloud.” By utilizing virtualization, this technology permits the operation of numerous virtual networks on a single physical network infrastructure. Cloud network technology essentially removes the need for complex on-premises infrastructure by abstracting the intricacies of the underlying hardware and giving customers flexible, on-demand access to resources.
Virtual private networks (VPNs), software-defined networking (SDN), cloud networking services, and cloud-based routers are the essential elements of cloud network technologies. Together, these elements guarantee improved security, smooth connectivity, and effective data transfer between end users and cloud-based services. Cloud network technology allows enterprises to accomplish more agility, lower operating costs, and scale their operations dynamically to suit changing business needs by separating the actual infrastructure from the network services.
The Development and Extension of Cloud Networking
Physical gear, including routers, switches, and dedicated lines, was a major component of traditional networking and was frequently costly and difficult to expand. Cloud networking has evolved through major technological breakthroughs and conceptual shifts in IT architecture. A revolutionary age in networking began with the advent of virtualization in the early 2000s, which reduced costs, maximized resource efficiency, and allowed for the operation of numerous virtual instances on a single physical machine.
Since cloud computing gained popularity, there has been an increasing need for more adaptable and scalable networking solutions. As a result, networking solutions that are cloud-native and tailored to the particular needs of cloud environments have been developed. The introduction of network functions virtualization (NFV) and software-defined networking (SDN) are significant turning points in the development of cloud networking. By separating the network control plane from the data plane, SDN makes it possible to manage network resources centrally and programmably. NFV, on the other hand, increases flexibility and lessens reliance on hardware by substituting software-based solutions for conventional network appliances.
Benefits and Significance of Cloud Network Technology
Cloud networks are becoming an essential component of contemporary IT architecture, providing a plethora of benefits that are vital to companies operating in the current digital environment. Its importance stems from its capacity to offer networking solutions that are scalable, adaptable, and reasonably priced—all of which are necessary to support digital transformation projects and dynamic company operations.
- Scalability and Flexibility: The innate scalability and flexibility of cloud network technology is one of its biggest advantages. In contrast to traditional networking, which frequently necessitates a large initial investment in physical infrastructure in order to scale, cloud networking enables businesses to quickly grow or shrink their network resources in response to demand. Businesses that deal with varying workloads or seasonal traffic spikes will find this elasticity especially helpful as it allows them to minimize resource utilization and prevent over-provisioning.
- Cost-effectiveness: The use of cloud network technology eliminates the need for large capital investments in hardware and upkeep. Businesses can reduce operational expenses and allocate more funds to strategic projects and innovation by utilizing a pay-as-you-go model. Further reducing costs is the lower energy usage and maintenance associated with the decreased requirement for physical infrastructure.
- Enhanced Security: To safeguard data and applications, contemporary cloud network technology integrates cutting-edge security methods including identity and access management (IAM), encryption, and zero-trust security models. Strong security monitoring and compliance standards are frequently used by cloud providers to protect sensitive data from cyber attacks and illegal access. Businesses managing sensitive client data or those in regulated industries especially need to prioritize this degree of protection.
- Enhanced Cooperation and Availability: Cloud network technology makes it easier for people to collaborate and work remotely by allowing them to access data and apps from any location with an internet connection. With the ability to collaborate in real-time and obtain the resources they require without geographical restrictions, employees may work more productively and support distant teams thanks to this accessibility.
- Disaster Recovery and Business Continuity: By offering redundant infrastructure and automated backup solutions, cloud network technology improves disaster recovery and business continuity capabilities. Businesses can promptly resume operations and reduce downtime in the event of a hardware malfunction or natural disaster, guaranteeing continuity of service and safeguarding vital data.
Comprehending Cloud Storage and Processing Capabilities

These two are essential elements of cloud network technology, and they are vital to the way businesses handle, store, and use data. These assets serve as the foundation for numerous cloud services, giving companies the ability to use scalable and effective IT solutions.
Clarifying Cloud Storage
A cloud storage service model stores data not on local servers or personal PCs, but rather on distant servers that may be accessed online. These distant servers, which are usually run by outside cloud service providers, provide elastic and scalable storage options that are simple to modify in accordance with customer needs. High availability, resilience, and security are features built into cloud storage, guaranteeing that data is safe from loss or unwanted access and always available when needed.
Among the main attributes of cloud storage are:
- Elasticity and Scalability: Without requiring the purchase of extra hardware, cloud storage solutions enable businesses to handle fluctuating data loads by automatically scaling up or down in response to demand.
- Data Redundancy and Backup: To safeguard data from hardware malfunctions and other potential disruptions, the majority of cloud storage services come with integrated redundancy and automated backup features.
- Collaboration and Accessibility: Cloud-stored data may be accessed by users from any internet-connected device, allowing for distant work and collaboration.
Typical categories of cloud storage consist of:
- Object storage: Made to manage massive volumes of unstructured data, including backups and multimedia files. Amazon S3 and Google Cloud Storage are two examples.
- Block Storage: Fit for applications like virtual machines and databases that need high-performance, low-latency storage. Azure Disk Storage and Amazon EBS are two examples.
- File Storage: It is perfect for shared file storage and collaborative work situations since it offers a hierarchical file system. Google Filestore and Amazon EFS are two examples.
An explanation of Cloud Computing Resources
Cloud service providers offer a range of computational and processing capacities for cloud computing resources. Businesses don’t need a large on-premises infrastructure to operate apps, handle data, and carry out intricate computations thanks to these resources.
Among the primary characteristics of cloud computing resources are:
- On-Demand Availability: Users can provide and scale computing resources as needed without making long-term commitments because they are available on-demand.
- Pay-As-You-Go Pricing: Because users only pay for the resources they use, cloud computing is an affordable way to handle varying workloads.
- Flexibility and Customization: A vast number of configurations and possibilities are provided by cloud computing services, allowing enterprises to customize resources to meet their unique requirements.
Typical categories of cloud computing resources consist of:
- Compute Instances: Virtual computers that offer the RAM and processing capacity required to run applications. Google Compute Engine and Amazon EC2 are two examples.
- Computing without a server: a setup where the infrastructure is automatically maintained by the cloud provider, freeing developers to concentrate on writing code rather than managing servers. Azure Functions and AWS Lambda are two examples.
- Kubernetes and containers: Software modules that are lightweight and portable that combine an application with all of its dependencies to enable consistent deployment in various settings. An orchestration tool called Kubernetes is used to scale containerized applications. Azure Kubernetes Service and Google Kubernetes Engine are two examples.
- AI and machine learning services:platforms and tools available in the cloud that offer pre-made models and frameworks for creating and implementing AI applications. AWS SageMaker and Google AI Platform are two examples.
Advantages of Cloud Computing and Storage
Numerous advantages that improve IT capabilities and corporate operations are provided by these resources:
- Cost Savings: By removing the need for large upfront hardware investments and lowering ongoing maintenance expenses, cloud resources offer significant cost savings.
- Flexibility and Scalability: Organizations may effortlessly adjust their resource levels in response to demand, guaranteeing maximum efficiency and lowest costs.
- Enhanced Security and Compliance: Top cloud service providers help businesses protect sensitive data and adhere to legal obligations by putting strong security measures in place and following industry standards.
- Enhanced Agility and Innovation: Businesses can develop more quickly and adapt to changes in the market more successfully when they can swiftly install and scale apps.
- Enhanced Cooperation and Availability: Cloud-based resources enable uninterrupted access to information and programs, facilitating remote work and augmenting cooperation among dispersed groups.
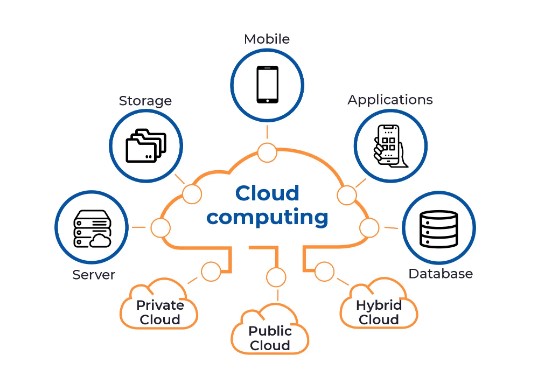
Cloud Networking Types
Several forms of cloud networking are available to meet diverse business requirements and IT environments. Knowing the differences between public, private, and hybrid cloud networking can help businesses choose the infrastructure that best suits their needs.
Networking in Public Clouds
Under this paradigm, services are made available to anyone who wishes to buy or use them via the public internet by third-party providers. These services are very scalable and economical, and they are usually provided through shared infrastructure. The public cloud market is dominated by big players like Google Cloud Platform (GCP), Microsoft Azure, and Amazon Web Services (AWS).
Public cloud networking has a number of benefits. First off, because there are no maintenance or capital expenditure requirements for hardware, it offers substantial cost savings. Companies only pay for the resources they use, which makes it an adaptable solution for handling varying workloads. Second, a large degree of scalability is provided by public cloud services, which enables companies to promptly adapt their resources to shifting demands. Startups and expanding businesses who need to scale operations quickly without being constrained by physical infrastructure would especially benefit from this.
Furthermore, public cloud networking makes it simple to access a variety of cutting-edge services and technologies, including big data analytics, machine learning, and IoT platforms, all of which can spur creativity and improve corporate operations. Leading providers of public cloud networking adopt strong security measures and follow industry standards to safeguard data and applications from cyber attacks. Security and compliance are also important components of public cloud networking.
Networking in Private Clouds
Cloud infrastructure that is dedicated to a single enterprise and provides improved control, security, and customisation is referred to by this paradigm. The infrastructure for this approach is not shared with other businesses, in contrast to public clouds, and it can be hosted on-site or by a third party provider.
The high degree of security and privacy that private cloud networking offers is one of its main advantages; this makes it perfect for companies that handle sensitive data or have strict regulatory requirements. Because they have total control over their infrastructure, organizations may tailor resource management, compliance procedures, and security settings to meet their unique requirements.
Networking for Hybrid Clouds
Combining public and private clouds into one adaptable system that takes use of both settings is known as hybrid cloud computing. This strategy enables enterprises to use the public cloud’s scalability and cost-effectiveness for workloads that are less sensitive and in situations of peak demand, all while retaining control over their vital apps and sensitive data in a private cloud.
Flexibility and balance are hybrid cloud networking’s main advantages. By distributing workloads across public and private clouds according to particular needs, such security, performance, and cost, it helps enterprises to optimize their IT infrastructure. To maintain compliance with data security rules, sensitive customer data, for example, might be housed in a private cloud. Meanwhile, high-volume, less sensitive apps can run on the public cloud to benefit from its scalability.
Because hybrid cloud networking offers different deployment settings, it also improves business continuity and disaster recovery plans. Businesses may swiftly move workloads to another environment in the case of an environment loss, avoiding downtime and preserving service availability.
Networking across Multiple Clouds
Multi-cloud leverages many public cloud services from various providers, in contrast to hybrid cloud, which blends private and public clouds. Using services from several cloud providers to maximize performance, cut expenses, and improve resilience is known as multi-cloud networking. Businesses can avoid vendor lock-in with this strategy, giving them more freedom and options when choosing services.
Leveraging the strengths of many cloud providers is the main benefit of multi-cloud networking. For instance, a company may choose to work with one supplier because of its strong data analytics tools and another because of its better machine learning skills. By using cloud services sparingly, workload performance and cost effectiveness can be maximized. Moreover, multi-cloud techniques improve disaster recovery and redundancy. Organizations can reduce the risk of downtime or data loss caused by an outage or failure of a single provider by spreading workloads among several providers. Because businesses can select the appropriate cloud service for each unique work, ensuring optimal performance and cost-effectiveness, this method also enables more smart resource allocation.
Requirements for data sovereignty and regulatory compliance are also supported by multi-cloud networking. To comply with local requirements, organizations can store and process data in specified geographic regions, which can improve data governance and compliance operations. Furthermore, because organizations aren’t dependent on a single vendor for all of their cloud needs, this strategy gives them more negotiating leverage and bargaining power with cloud providers.
Virtual Cloud Private (VPC)
A virtual private cloud (VPC) combines the advantages of public and private clouds into a safe, isolated area of a public cloud environment. By establishing a virtualized network environment where users can choose their own network architecture, including subnets, route tables, and access rules, VPCs provide more protection and control.
The capacity of VPCs to offer a high degree of security and compliance is one of its main advantages. Businesses can apply strict security measures, including firewalls, VPNs, and network access controls, to secure critical data and applications by isolating network resources within a specialized virtual network. With the ability to manage data flow and access within their VPC, enterprises may further assure compliance with regulatory standards thanks to this isolation.
Significant scalability and flexibility are also provided by VPCs. Businesses can simply modify their virtual private cloud (VPC) setups to adapt to evolving business requirements, such as demand-driven resource scaling. Businesses that are growing or have dynamic workloads will especially benefit from this scalability, which makes it possible for them to effectively manage their infrastructure without having to make large upfront investments.
Neighborhood Cloud Networking
In this arrangement, multiple firms with related objectives and goals—many from the same industry or with similar regulatory or compliance requirements—share cloud infrastructure. This paradigm offers a collaborative environment that enables cost savings, shared expertise, and increased compliance by combining the advantages of private and public clouds.
Community cloud networking’s main benefit is its capacity to meet particular industrial demands and legal obligations. Organizations inside a community cloud can create customized solutions to solve their specific operational and regulatory concerns by combining resources and expertise. Cost-sharing is another benefit of this cooperative strategy, which gives individual firms access to cutting-edge cloud services and technologies while also lessening their financial burden.
Additionally, community clouds encourage uniformity and communication among participating enterprises. By cooperating inside a shared cloud environment, businesses can create common standards and practices that will facilitate more seamless data interchange and cooperation. Processes within the community can be streamlined and operational efficiency increased by this standardization.
Consent Manager and Cloud Networking
Consent management system integration with cloud networking is becoming more and more crucial. Keeping users’ trust and adhering to data privacy laws are crucial as companies gather and handle enormous volumes of personal data. Cloud networking gives enterprises the capacity to handle consent data securely and effectively by providing the infrastructure required to enable complex consent management systems.
The procedures and tools used by companies to secure, monitor, and oversee user consent for data processing operations are referred to as consent management systems. This is necessary in order to abide by laws such as the California Consumer Privacy Act (CCPA) in the US and the General Data Protection Regulation (GDPR) in the EU, which require businesses to get users’ express consent before collecting or processing their personal data.
Cloud networking's function in consent management
Because cloud networking offers a scalable, adaptable, and safe infrastructure, it significantly improves the capabilities of consent management systems. Cloud networking enables enterprises to implement consent management systems that can readily scale to meet expanding user bases and regulatory needs. These solutions can handle substantial volumes of consent data.
Increased scalability is one of the main advantages of combining cloud networking and consent management. Businesses can scale their consent management systems up or down in response to demand thanks to cloud infrastructure, which guarantees that they can manage surges in user activity or modifications in regulatory requirements without suffering from appreciable infrastructure price increases or delays. This flexibility is especially useful for multinational corporations that have consent management to handle across several governments and regions.
Cloud Network Technology's Components
A number of essential elements make up cloud networking technology, which when combined offers reliable, scalable, and effective networking solutions for companies. Gaining the most out of cloud services and streamlining IT infrastructure requires an understanding of these elements.
Cloud Network Technology's Components

A number of essential elements make up cloud networking technology, which when combined offers reliable, scalable, and effective networking solutions for companies. Gaining the most out of cloud services and streamlining IT infrastructure requires an understanding of these elements.
Summary of the Elements
Cloud infrastructure, virtualization technologies, networking services, and security frameworks are the fundamental elements of cloud network technology. These components serve as the cornerstone of cloud networking, providing improved security, effective resource management, and seamless communication.
- Cloud Infrastructure: The term “cloud infrastructure” describes the digital and hardware assets that enable cloud computing services. Servers, networking hardware, storage systems, and data centers are all included. Because cloud infrastructure is highly scalable, resources can be assigned dynamically in response to demand.
- Technologies related to virtualization: Several virtual instances can operate on a single physical server thanks to virtualization, which is a major enabler of cloud network technology. By abstracting the underlying hardware, this technology produces easily maintained and scalable virtual machines (VMs) and virtual networks. A key component of virtualization are hypervisors, which are software systems that build and oversee virtual computers.
- Networking Services: Virtual private networks (VPNs), software-defined networking (SDN), and network functions virtualization (NFV) are examples of networking services. Secure connectivity between distant users and cloud resources is made possible by VPNs. Centralized network traffic management is made possible with SDN’s separation of the control plane and data plane. NFV increases flexibility and lessens reliance on hardware by substituting software-based solutions for conventional network devices.
- Security Frameworks: An essential part of cloud network technology is security. Firewalls, intrusion detection and prevention systems (IDPS), identity and access management (IAM), and encryption are examples of security frameworks. Data, apps, and network resources are shielded from cyberattacks and unwanted access by these technologies and protocols.
- Tools for Cloud Management: These programs make it easier to keep an eye on, manage, and maximize cloud resources. They facilitate effective cloud operations and proactive issue resolution by offering insights into resource use, performance indicators, and security status.
Models of Cloud Computing
Cloud computing paradigms dictate how cloud services are organized and delivered. Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS) are the main models.
- Infrastructure as a Service (IaaS): IaaS, or infrastructure as a service, uses the internet to deliver virtualized computer resources. With the help of basic building elements like networks, storage, and virtual machines, this paradigm enables companies to create and maintain their own IT infrastructure. Because of its great scalability and flexibility, IaaS is appropriate for workloads requiring large amounts of processing power and unique configurations. IaaS vendors include Google Compute Engine, Microsoft Azure Virtual Machines, and Amazon Web Services (AWS) EC2.
- Platform as a Service (PaaS): PaaS gives developers a platform to create, launch, and maintain apps without having to worry about the supporting infrastructure. With this architecture, developers may concentrate on code and application logic because it encompasses databases, middleware, operating systems, and development frameworks. PaaS shortens time-to-market, simplifies the development process, and lowers complexity. Heroku, Microsoft Azure App Service, and Google App Engine are well-known PaaS vendors.
- Software as a Service (SaaS): SaaS offers subscription-based online software application delivery. These programs are accessible through web browsers and don’t require installation or upkeep for users. SaaS models are perfect for a variety of corporate applications due to their ease of use, scalability, and automatic upgrades. Salesforce, Microsoft Office 365, and Google Workspace are a few SaaS examples.
Every cloud computing model has unique benefits and fits various use cases and business requirements. IaaS is best suited for companies with specialized IT needs and knowledge because it offers enterprises complete control over the infrastructure. PaaS takes away a large portion of infrastructure administration, freeing developers to concentrate on creating innovative applications. SaaS provides end users with quick setup times and fully managed software solutions.
Cloud Networks and Virtualization
A key component of cloud networking is virtualization, which makes it possible to create several virtual instances on a single physical hardware resource. By isolating and abstracting various computer environments, this technique permits them to operate simultaneously on a common physical infrastructure.
Increased flexibility, economic effectiveness, and resource utilization are just a few advantages of virtualization. Virtualization enables companies to make the most of their physical resources by separating software from the underlying hardware, which lowers the need for further hardware purchases. As a result, there are large financial savings on both initial capital costs and continuing maintenance.
Virtualization also improves cloud networks’ scalability and flexibility. Virtual machines (VMs) and applications can be swiftly provisioned and deployed by organizations, allowing them to respond fast to changes in workload and shifting business demands. Businesses that need scalable solutions to support growth and changing operational requirements will find this agility especially helpful.
Cloud Network Storage
Another crucial element of cloud network technology is storage, which makes data accessible and manageable in dispersed contexts. Cloud storage solutions are made to offer safe, dependable, and scalable storage choices to satisfy the various demands of contemporary businesses.
Cloud storage: Generally speaking, there are three primary categories of cloud storage: object, block, and file. Each class is appropriate for particular use scenarios and fulfills distinct functions.
Object storage: Large volumes of unstructured data, including backups, logs, and multimedia files, are best stored in object storage. It offers strong data durability and availability and is very scalable. Services for object storage include Google Cloud Storage and Amazon S3.
File storage: Because file storage offers a hierarchical file system, shared file storage and collaborative work environments can benefit from it. It works with workloads and file-based programs that need to be conversant with the file system interface. Services for storing files include Google Filestore and Amazon EFS.
Block storage: Applications like databases and virtual machines that need high-performance, low-latency storage use block storage. Because it offers direct access to storage blocks, performance and data placement may be precisely controlled. Azure Disk Storage and Amazon EBS are two popular block storage providers.
Cloud Network Technology Connectivity
Connectivity makes it possible for cloud resources, apps, and end users to communicate and transfer data seamlessly. Sustaining the performance, dependability, and security of cloud networks requires effective connectivity solutions.
Cloud connectivity : There are several ways to connect to the cloud, including via hybrid connections, private networks, and the Internet. Various performance, security, and cost levels are provided by each method, meeting a range of business needs.
Internet-based connectivity : Having internet access is the most popular and extensively utilized way to use cloud services. It offers wide accessibility and works well with a variety of workloads and applications. Internet-based connections, however, are less suitable for delicate or mission-critical tasks due to their susceptibility to latency and security threats.
Private connectivity : Private connectivity alternatives that create direct connections between an organization’s on-premises infrastructure and cloud services, including virtual private networks (VPNs) or dedicated leased lines, offer improved security and performance. These connections are frequently utilized for applications that demand high performance and security because they offer reliable, low-latency access to cloud services.
Security of Cloud Networks
To guarantee the availability, confidentiality, and integrity of cloud resources, strong security measures are necessary. An essential component of cloud computing is cloud network security management, which focuses on safeguarding infrastructure, data, and apps from dangers and weaknesses. Firewalls, Virtual Private Clouds (VPCs), Identity and Access Management (IAM), and data encryption are important elements of cloud network security.
Identity and Access Management (IAM)
IAM is essential to cloud security because it controls access to cloud resources and manages user identities. This is a set of technological and policy guidelines that guarantee the proper people and organizations have access to technology resources.
IAM systems perform numerous vital tasks, including:
- User Authentication: When a user tries to access cloud resources, IAM systems confirm their identity. Credentials like usernames, passwords, multi-factor authentication (MFA), or biometric verification are usually used for this. By requesting several kinds of identity from users, MFA is especially good at boosting security.
- Access Control: IAM systems establish and implement policies that specify the resources that users are allowed to access as well as the actions they are allowed to do. One popular method is Role-Based Access Control (RBAC), which distributes access according to user roles inside the company. This lowers the possibility of unwanted access by guaranteeing that users have the minimal access required to complete their duties.
- Provisioning and De-provisioning of Users: IAM handles the creation, modification, and removal of user accounts and permissions automatically. The automation aids in the maintenance of precise and current access controls, particularly in the event of employee changes in responsibilities within the business or their departure.
- Monitoring and Auditing: To keep tabs on user behavior and access patterns, IAM systems come with logging and monitoring features. These records are crucial for spotting unusual activity, looking into security incidents, and making sure legal requirements are met.
Organizations may greatly improve the security of their cloud networks by putting strong IAM procedures in place, which will guarantee that only authorized users can access resources and sensitive data.
Virtual Private Clouds (VPCs) and Firewalls
These two are essential parts of cloud network security because they offer network segmentation and perimeter protection to shield cloud resources from cyberattacks and unwanted access.
Firewalls: A trustworthy internal network and an untrusted external network, such as the Internet, are separated by firewalls. They use preset security rules to monitor and manage all incoming and outgoing network traffic. Firewalls can be deployed in cloud environments as software or hardware programs that are frequently included in cloud service packages.
Cloud firewalls provide a number of important functions:
- Traffic Filtering: In accordance with security regulations, firewalls examine network traffic and weed out unwanted or malicious content. This aids in the defense against assaults like SQL injection, cross-site scripting, and distributed denial of service (DDoS) (XSS).
- Intrusion Detection and Prevention: Systems known as intrusion detection and prevention systems, or IDPS, are a feature of advanced firewalls. They scan network traffic for unusual activity and automatically block possible attacks.
- Application-Level Protection: By giving businesses fine-grained control over application traffic, firewalls enable them to impose security rules that are tailored to the needs of certain services and applications.
- Virtual Private Clouds (VPCs): Within a public cloud, VPCs offer a segregated virtual network environment. Enhanced control over network traffic and security is made possible by VPCs, which let businesses build their own network architecture, including subnets, route tables, and security groups.
Key advantages of VPCs consist of:
- Network Isolation: In the public cloud, virtual private clouds (VPCs) separate network resources from other tenants, lowering the possibility of cross-tenant data breaches and guaranteeing the privacy and security of network traffic.
- Customizable Security Controls: Virtual private clouds (VPCs) allow enterprises to set up unique security rules, such security groups and access control lists (ACLs), to manage traffic and prevent access to particular resources.
- Secure Connectivity: Virtual Private Clouds (VPCs) facilitate the establishment of secure connections between an organization’s on-premises infrastructure and cloud resources by supporting secure connectivity options including VPNs and Direct Connect.
When combined, firewalls and VPCs offer a strong defense-in-depth approach that improves cloud network security and resilience.
Data Encryption
By transforming data into an unreadable format, encryption aids in preventing unwanted access to data. Data is protected and rendered unreadable by encryption, even in the event that it is intercepted or accessed by unauthorized individuals.
In cloud environments, there are two main methods of data encryption:
Data at Rest Encryption: This kind of encryption guards information kept on tangible media, such SSDs, hard disks, and cloud storage accounts. Data at rest encryption secures stored data by encrypting files and databases using algorithms. For data that is at rest, cloud providers usually have built-in encryption options, making it easy for businesses to protect their data.
Data in Transit Encryption: This type of encryption shields information while it travels over networks, such those connecting a user’s device to cloud servers or various cloud services. Common protocols used to encrypt data in transit include Secure Sockets Layer (SSL) and Transport Layer Security (TLS), which offer safe communication routes that guard against manipulation and eavesdropping.
Several crucial procedures are involved in implementing encryption in cloud environments:
- Encryption Key Management: Secure encryption key production, distribution, rotation, and storage are necessary for effective encryption. Key management services (KMS), which automate key management tasks and improve security, are frequently offered by cloud providers.
- End-to-end encryption: This type of encryption makes sure that information is encrypted from the beginning and stays that way while it is being sent and stored. By guaranteeing that data is decrypted by the designated receiver only, this offers an increased degree of security.
- Compliance & Regulatory Requirements: Encryption assists businesses in adhering to laws like the CCPA, GDPR, and HIPAA that protect personal information. Sustaining client confidence and avoiding legal ramifications require strict adherence to these regulations.
Tools for Automation and Management
Optimizing cloud network operations, guaranteeing optimum resource use, and improving overall service delivery all depend on effective management and automation technologies. These tools have a wide range of features, including as resource management, automation and orchestration, and service management, all of which are essential to preserving the dependability and performance of cloud systems.
Management of Resources
Effectively allocating, monitoring, and optimizing cloud resources—such as computers, storage, and network components—is the goal of cloud networking resource management. This procedure is essential for preserving peak efficiency, keeping expenses under control, and guaranteeing that resources are available to satisfy corporate demands.
Tools for managing cloud resources offer numerous essential features, including:
Provisioning and De-provisioning: Allocating and releasing resources in response to demand is automated by these tools, which are known as provisioning and de-provisioning. While de-provisioning helps to free up unwanted resources, cut expenses, and avoid resource sprawl, automated provisioning guarantees that resources are available when needed.
Monitoring and Analytics: Tools for resource management provide extensive functionality for tracking and analyzing data, giving users insight into how resources are being used, performance indicators, and possible bottlenecks. By using these insights, IT professionals can ensure that cloud environments function well by making well-informed decisions around resource allocation and optimization.
Capacity Planning: Capacity planning, which forecasts future resource needs based on past usage patterns and projected expansion, is an essential component of effective resource management. Through careful planning, companies may make sure they have the resources they need to sustain their operations without going overboard.
Cost management: Tools for resource management frequently have cost management functions that monitor the use and costs of resources. These attributes facilitate the identification of cost-saving prospects by companies, such as the appropriate sizing of resources or the execution of cost optimization tactics.
Orchestration and Automation
These technologies automate tedious processes and coordinate intricate workflows, streamlining and simplifying the management of cloud network operations. These instruments improve service delivery speed, minimize human error, and increase operational efficiency.
Automation Tools: Provisioning, scalability, and configuration management are examples of regular processes that automation is intended to automate. Organizations can decrease manual labor, increase consistency, and guarantee effective management of cloud resources by automating these operations.
Among the main advantages of automation tools are:
- Scalability: By using pre-established policies and triggers, automation allows businesses to automatically scale resources up or down. This increases responsiveness and scalability by ensuring that resources are dynamically modified to match shifting demand.
- Consistency: Tasks are carried out precisely and consistently thanks to automated processes, which lower the possibility of configuration errors and increase overall reliability.
- Time Savings: IT teams may concentrate on more strategic activities and projects by automating repetitive procedures, which saves time.
- Orchestration Tools: Using a variety of cloud resources and services, orchestration tools manage and coordinate the execution of intricate workflows. By ensuring that various parts of an application or service function together cohesively, these tools improve performance and efficiency.
Among the main advantages of orchestration tools are:
- Workflow Management: Using orchestration tools, businesses may create and oversee processes that cut across various cloud services and resources. This guarantees that dependencies are properly maintained and that processes are carried out in the right order.
- Service Integration: Orchestration makes it easier to combine several cloud apps and services so that they function as a single unit to provide a service.
- Resource Optimization: Orchestration technologies help maximize resource consumption and enhance overall service performance by coordinating the execution of tasks and workflows.
Service Management
It entails managing and supervising cloud services to guarantee they fulfill user expectations and organizational objectives. Managing service delivery, performance, availability, and support falls under this category.
Tools for cloud service administration offer numerous crucial features, including:
Service Monitoring: These solutions provide real-time insights and alerts about any problems by continuously monitoring the availability and performance of cloud services. By proactively identifying and addressing issues, service monitoring enables businesses to maintain high levels of service performance and availability.
Incident Management: Tools for service management come with incident tracking and management capabilities. IT personnel can immediately identify and fix problems thanks to these features, which reduces downtime and guarantees a prompt return to regular operations.
Service Level Management: To guarantee that cloud services fulfill predetermined performance and availability criteria, effective service management entails creating and keeping an eye on service level agreements (SLAs). Tools for service level management assist businesses in monitoring SLA compliance and, if required, taking remedial action.
Change Management: By monitoring and controlling modifications to cloud services and infrastructure, service management tools assist with change management procedures. This guarantees that modifications are carried out efficiently and with the least possible impact on services.
Self-Service and User Support: Ticketing systems and self-service portals are examples of user support features that are frequently included in service management software. These features allow users to manage their own service needs and request assistance. These functions lessen the workload for IT support personnel while increasing user satisfaction.
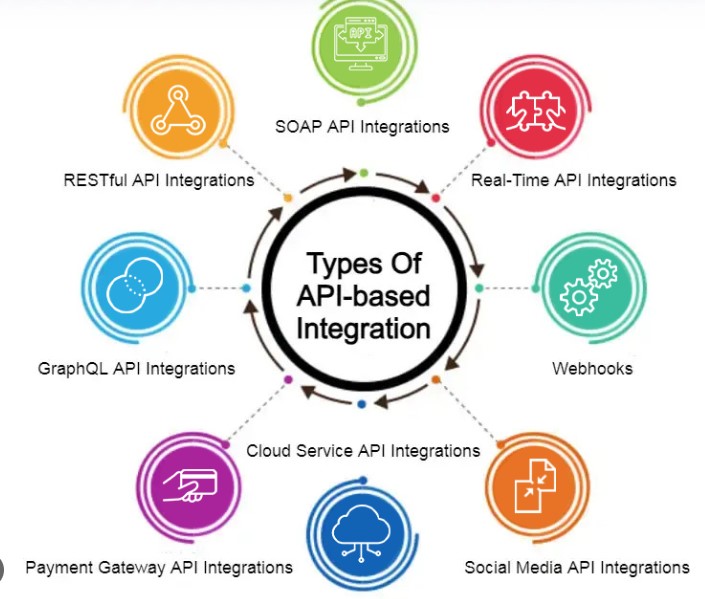
Cloud APIs
In order to provide smooth communication between various cloud services and apps, APIs are crucial tools. These APIs give developers defined instructions and protocols for effectively integrating, managing, and automating cloud resources. Businesses may improve the functionality, scalability, and flexibility of their cloud infrastructure by utilizing cloud APIs.
APIs for Networking
These APIs are essential for controlling and setting up cloud network resources. They offer features for configuring load balancers, subnets, virtual networks, and network security groups. Through networking APIs, customers can improve cloud environment security, optimize traffic flow, and automate network configuration. Organizations can ensure optimal performance and connection by dynamically adjusting network settings to meet changing demands by utilizing networking APIs. AWS VPC API, Google Cloud VPC API, and Azure Virtual Network API are examples of common networking APIs. Through the control of elements including firewall rule setups, routing table updates, and IP address allocation, these APIs simplify network administration and raise the general effectiveness of cloud infrastructure.
APIs for Databases
Because of the way they are made to work with cloud-based database services, developers can use them to do database operations programmatically. These APIs help users manage database schemas, run queries, and create, read, update, and delete (CRUD) database records. Database APIs give you the tools you need to improve data accessibility, automate database maintenance activities, and make sure databases integrate seamlessly with applications. They support relational, NoSQL, and in-memory databases, among other database formats. The Azure SQL Database API, Google Cloud SQL API, and Amazon RDS API are a few examples of database APIs. These APIs enable applications that need scalable and dependable data storage solutions by making it easier to handle cloud databases.
APIs for Storage
Developers can list, upload, download, and remove files or objects from cloud storage services using these APIs. Advanced capabilities like data replication, storage bucket management, and access control setting are also supported by storage APIs. Organizations may ensure effective data management and accessibility by integrating cloud storage into their applications effortlessly through the use of storage APIs. Popular storage APIs include the Azure Blob Storage API, Google Cloud Storage API, and Amazon S3 API. They all offer strong capabilities for a range of use cases and storage requirements, from straightforward file storing to intricate data archiving and retrieval.
Compute APIs
They enable programmatic creation, configuration, and management of virtual machines (VMs) and other computing instances by developers. With the help of these APIs, users can efficiently manage the lifespan of virtual instances, scale workloads up or down in response to demand, and automate the deployment of compute resources. The capability required to manage operations like starting, halting, resizing, and monitoring virtual machines is provided by compute APIs. Consider the popular compute APIs for AWS EC2, Google Compute Engine, and Azure Virtual Machines. These APIs facilitate a range of automation and integration scenarios, improving the effectiveness and responsiveness of cloud-based applications.
Identity and Access Management (IAM) APIs
In cloud environments, IAM APIs are essential for managing user management, authorization, and authentication. By giving administrators the means to manage cloud resource access, these APIs guarantee that sensitive data and services can only be accessed by approved users and applications. IAM APIs facilitate a number of operations, such as credential management, role assignment, policy enforcement, and user creation and maintenance.
Because IAM APIs enable organizations to set granular access controls based on user roles and permissions, they make it easier to implement strong security policies. By ensuring that users possess the necessary level of access to carry out their jobs, this reduces the possibility of illegal access and possible security breaches. AWS IAM API, Google Cloud IAM API, and Azure Active Directory API are a few notable examples that offer a wide range of capabilities for cloud environment identity and access control management.
APIs for Application Development
They facilitate the effective development, deployment, and management of apps by developers in cloud settings. A vast array of functionalities, including those related to coding, testing, deployment, monitoring, and scalability, are supported by these APIs for different areas of application development.
Developers can use cloud-based resources like databases, storage, messaging services, and machine learning models by integrating cloud services into apps more easily with the help of Application Development APIs. For instance, developers may design serverless apps that dynamically grow in response to incoming requests, eliminating the need for traditional server management and improving application performance, thanks to APIs like AWS Lambda API, Google Cloud Functions API, and Azure Functions API.
By offering resources for automating the build, test, and deployment procedures, these APIs additionally facilitate continuous integration and continuous deployment (CI/CD) workflows. The time it takes to bring new features and apps to market is shortened, development cycles are sped up, and code quality is increased because to this connection. Furthermore, monitoring and logging features are frequently included in Application Development APIs, allowing developers to keep tabs on the performance of their applications, identify problems, and optimize resource utilization instantly.
Benefits of Networking in the Cloud
Numerous advantages provided by cloud network technology greatly improve business operations, reliability, and efficiency. Cloud networking has many benefits, such as lower costs, greater accessibility, and easier disaster recovery, which makes it a crucial part of today’s IT architecture.
Cost Efficiency
The affordability of cloud network technology is among its most alluring benefits. Businesses can lessen or do away with the requirement to make significant upfront investments in physical hardware and infrastructure by utilizing cloud services. Pay-as-you-go pricing models are provided by cloud providers, enabling businesses to pay only for the services they really use. This helps them cut expenses and eliminate wasteful spending. Because they can adjust resources to meet demand without incurring large costs, this strategy is especially advantageous for companies with variable workloads.
Additionally, operational expenses related to operating and maintaining on-premises infrastructure are decreased by cloud network technologies. By taking on the responsibility of hardware upkeep, upgrades, and energy use, the cloud provider frees up internal IT resources and funds for other important projects. Automated technologies for resource management and monitoring are frequently included in cloud services, which reduces administrative overhead and improves cost effectiveness.
Boost Your Accessibility
Because cloud network technology offers ubiquitous access to data and applications from any location with an internet connection, accessibility is greatly improved. With greater accessibility, employees may now work from anywhere at any time, contributing to the growing trend of remote work and global cooperation. Businesses can guarantee that their staff, no matter where they are physically located, has seamless access to the tools and information required to complete their duties by hosting applications and data on the cloud.
Software and update distribution and deployment are also made easier by cloud-based solutions. Cloud services provide automated updates and centralized management in place of conventional techniques that call for human installation and maintenance. This guarantees that all users always have access to the newest features and security improvements.
Assist with Disaster Recovery
Cloud network technology is essential for supporting business continuity and disaster recovery. Cloud services provide strong disaster recovery options that let companies swiftly minimize downtime and bounce back from disruptions. These solutions, which guard vital data and applications against loss or corruption, usually comprise automatic backup, data replication, and failover procedures.
The capability of cloud-based disaster recovery to replicate data across several geographical locations is one of its main advantages. Because of this geographic redundancy, key systems’ availability and integrity are maintained even in the event of a malfunction or outage at one data center. Data can be promptly restored from a different location. Cloud providers give enterprises a high degree of resilience and dependability since they frequently have large infrastructure and resources devoted to disaster recovery.
Scalability and flexibility are further features of cloud disaster recovery systems, enabling businesses to customize their recovery plans to suit unique demands and legal obligations. Companies can select from a variety of alternatives, such as multi-site replication, continuous data protection, and incremental backups, to make sure that their operational priorities and risk tolerance are met by their disaster recovery plans.
Updates for Software Automatically
They guarantee that systems and apps are always up to date with the newest features, security updates, and performance enhancements, which is a major benefit of cloud network technology. With this feature, IT personnel may no longer manually intervene, which lessens their workload and lowers the possibility of vulnerabilities resulting from out-of-date software.
Updates in cloud settings are usually scheduled and deployed by the service provider in a seamless manner, frequently without interfering with the user experience. By ensuring high consistency and dependability, this automatic update method makes sure that all users throughout the business take advantage of the most recent developments and security precautions at the same time.
Automatic updates also improve an organization’s overall security posture by quickly resolving newly identified threats and vulnerabilities. Cloud services assist defend against cyberattacks and data breaches by guaranteeing that all systems are promptly patched and updated, thus lowering the chance of security events.
Improved Cooperation
Regardless of their physical location, users may readily share files, discuss ideas, and collaborate in real-time using cloud-based collaboration tools and platforms.
Elements like project management, instant messaging, video conferencing, and shared document editing are common elements of cloud collaboration tools, and they all let team members communicate and work together more easily. Teams may work together productively on projects and tasks thanks to platforms like Google Workspace, Microsoft Teams, and Slack, which include a variety of collaboration functions.
Because cloud collaboration solutions are real-time, all team members may instantly participate in debates and decision-making processes and have access to the most recent information. Teams benefit from this immediacy, which increases their agility and responsiveness and helps them take advantage of opportunities and solve problems faster.
Reduced IT Maintenance
Internal IT teams will be more innovative and productive as a result of this shift, which frees them up to concentrate on more strategic projects rather than standard maintenance duties. One major benefit of cloud network technology is reduced IT maintenance, since the cloud service provider bears much of the responsibility for infrastructure management, software updates, and system maintenance.
Cloud service providers take care of a number of IT maintenance tasks, such as system backups, security upgrades, hardware management, and network monitoring. With this all-inclusive support, the organization’s IT personnel doesn’t need to be directly involved in maintaining the underlying infrastructure’s efficiency and security.
Cloud technology lowers expenses for equipment purchase, energy use, and physical space by eliminating the requirement for on-premises hardware and related maintenance. Without having to worry about the costs and complications of managing more servers and storage devices, organizations may scale their infrastructure in response to demand.
Cloud Network Technology Drawbacks
Although cloud network technology has many advantages, there are drawbacks and difficulties as well. Dependency on internet access, privacy and security problems, control limitations, and vendor lock-in are important difficulties. Businesses must be aware of these disadvantages in order to make wise choices about cloud adoption and management techniques.
Dependence on Internet Access
The fact that cloud network technology depends on dependable internet access is one of its main drawbacks. Since cloud services can only be accessible via the internet, losing access to vital apps and data can result from any disruption in connectivity. Because of this reliance, cloud services are susceptible to problems including bandwidth restrictions, latency, and network failures.
Relying heavily on cloud services might be risky for enterprises operating in areas with patchy or unreliable internet connectivity. Business continuity and productivity can be impacted by sporadic outages brought on by technological problems, natural catastrophes, or cyberattacks, even in places with strong internet connectivity.
In order to reduce these risks and guarantee ongoing access to cloud services, organizations frequently need to invest in redundant internet connections and failover systems. Some of the cost-saving advantages of adopting cloud computing may be negated, though, by these measures’ propensity to raise overall expenses and complexity.
Privacy and Security Issues
Businesses may be vulnerable to a range of security risks, such as data breaches, cyberattacks, and unauthorized access, if they store and handle sensitive data on the cloud. Public cloud systems are multi-tenant, meaning that several clients share the same infrastructure, which increases these risks.
Even with the implementation of strong security measures by cloud providers, businesses still bear the responsibility of safeguarding their data and guaranteeing adherence to pertinent rules. This duty entails putting robust access controls, encryption, and monitoring in place to protect data from potential dangers.
The possibility that data may be accessed by outside parties, such as cloud service providers and governmental organizations, gives rise to further privacy concerns. To make sure that cloud providers’ data privacy policies and practices meet their own compliance needs and privacy standards, businesses need to carefully assess these practices.
Limited Control
In cloud environments, the cloud provider manages and maintains a large portion of the infrastructure, which might limit the customer’s options for customization and control. Another significant drawback of cloud network technology is the limited control over cloud infrastructure and services.
For instance, companies might only be able to choose particular hardware parts, adjust network settings, or maximize performance metrics to a limited extent beyond what the cloud provider provides. Organizations that need customized solutions to address certain business objectives or those with special technological constraints may find this lack of control concerning.
Furthermore, there may be difficulties with risk management, data governance, and compliance if essential IT tasks are outsourced to a third party. Companies need to make sure that the cloud providers they use follow industry norms and laws as well as their own internal policies and guidelines.
Organizations frequently have to establish service level agreements (SLAs) that specify the degree of control and customization that may be had, along with the provider’s obligations on security, performance, and support, in order to allay these worries. SLAs can help achieve the required level of control, although doing so can be difficult and may not completely satisfy all organizational needs.
Lock-In of Vendors
Because of this dependence, it may be difficult to migrate workloads to different cloud environments or switch providers without having to spend a lot of money and time. One major drawback of cloud network technology is vendor lock-in, when companies are forced to use the infrastructure, services, and tools of only one cloud provider.
A number of things can lead to vendor lock-in, such as the usage of proprietary APIs, data formats, and administration tools unique to one cloud provider. These proprietary components may cause incompatibilities and make it more difficult to move data and apps to different cloud providers or on-premises settings.
Vendor lock-in can have major operational and financial ramifications. Re-architecting applications, retraining employees, and reconfiguring systems to operate with a new provider can come at a considerable cost to businesses. Large-scale data and application migrations can also be a time-consuming process that interferes with continuing business operations.
Organizations can use techniques including leveraging open standards and technologies, developing applications for portability, and employing a multi-cloud or hybrid cloud approach to reduce the risk of vendor lock-in. By reducing reliance on a single provider and increasing flexibility, these tactics can help businesses take advantage of the benefits of many cloud platforms while lowering the dangers of vendor lock-in.
Problems with Latency
The term “latency” describes the lag in time that occurs when data is transferred from the user’s device to the cloud server. Applications that require real-time processing and fast reaction times, such online gaming, video conferencing, and financial trading platforms, can be severely impacted by high latency. One significant drawback of cloud network technology is latency, which impairs the responsiveness and speed of services and apps accessed over the cloud.
In cloud environments, latency is caused by a number of factors, such as the network architecture of the cloud provider, the internet connection quality, and the physical distance between the user and the data center. Data packets may still need to travel across several networks and geographical locations even with a strong cloud architecture, which would increase the overall latency.
Businesses may endure less than ideal user experiences, lower productivity, and even revenue loss if crucial apps don’t operate as planned as a result of latency problems. Organizations can use content delivery networks (CDNs) to cache content closer to end users, choose cloud providers with data centers close to their user base, and deploy edge computing solutions—which process data closer to the source of data generation—as ways to reduce latency.
Although these steps can lower latency, they might also come with more expenses and complexity, which might outweigh part of the advantages of adopting cloud computing.
Difficulties with Compliance
Because cloud infrastructure is spread and third-party providers are involved, ensuring compliance with industry standards, regulations, and data protection laws can be challenging. Businesses implementing cloud network technologies face a great deal of compliance problems, especially those in highly regulated sectors like finance, healthcare, and government.
Ensuring data sovereignty, which necessitates that data be processed and stored within specified geographic bounds in order to comply with local rules, is one of the main compliance challenges. Businesses must choose their data storage locations carefully in order to comply with cloud providers’ policies, which frequently require them to have data centers across various regions.
Additionally, because cloud providers oversee the underlying infrastructure, it might be difficult to maintain visibility and control over data in the cloud. Organizations may find it challenging to successfully establish and enforce compliance policies and processes due to this lack of direct control. Businesses are forced to rely on the compliance guarantees and certifications provided by their cloud providers, which may not always completely match their unique compliance requirements.
Keeping up with different data protection laws, such the Health Insurance Portability and Accountability Act (HIPAA) in the US or the General Data Protection Regulation (GDPR) in the EU, is another difficulty. Strong compliance frameworks and ongoing monitoring are required to meet the strict data management, security, and breach reporting requirements imposed by these legislation.
Expenses are an Issue
Although cloud network technology is sometimes marketed as being cost-effective, many firms find it extremely difficult to control expenditures. Although flexible, if pay-as-you-go cloud service pricing is not carefully handled, it may result in unforeseen costs and overruns.
The possibility of resource sprawl, which occurs when underutilized or unused resources build up over time and result in needless costs, is one of the primary cost-related issues. In the absence of adequate supervision, companies could keep paying for resources that are overutilized or improperly configured, raising their total cloud expenses.
Furthermore, data transfer and egress fees can quickly mount up in expenses, particularly for applications involving substantial data movement between multiple cloud services or across countries. These costs can add up and are frequently disregarded in the early phases of planning, which results in unforeseen costs.
